Secrets and Environment Variables
We recommend using secrets to securely manage your application's secrets and environment variables in DBOS Cloud. Secrets are key-value pairs that are securely stored in DBOS Cloud and made available to your application as environment variables. Redeploy your application for newly created or updated secrets to take effect.
Managing and Using Secrets
You can create or update a secret using the Cloud CLI:
dbos-cloud app env create -s <secret-name> -v <secret-value>
A few secrets name are reserved and cannot be used. These are DBOS_DATABASE_URL and DBOS_APP_HOSTNAME.
For example, to create a secret named API_KEY with value abc123, run:
dbos-cloud app env create -s API_KEY -v abc123
When you next redeploy your application, its environment will be updated to contain the API_KEY environment variable with value abc123.
You can access it like any other environment variable:
- Python
- Typescript
key = os.environ['API_KEY'] # Value is abc123
const key = process.env.API_KEY; // Value is abc123
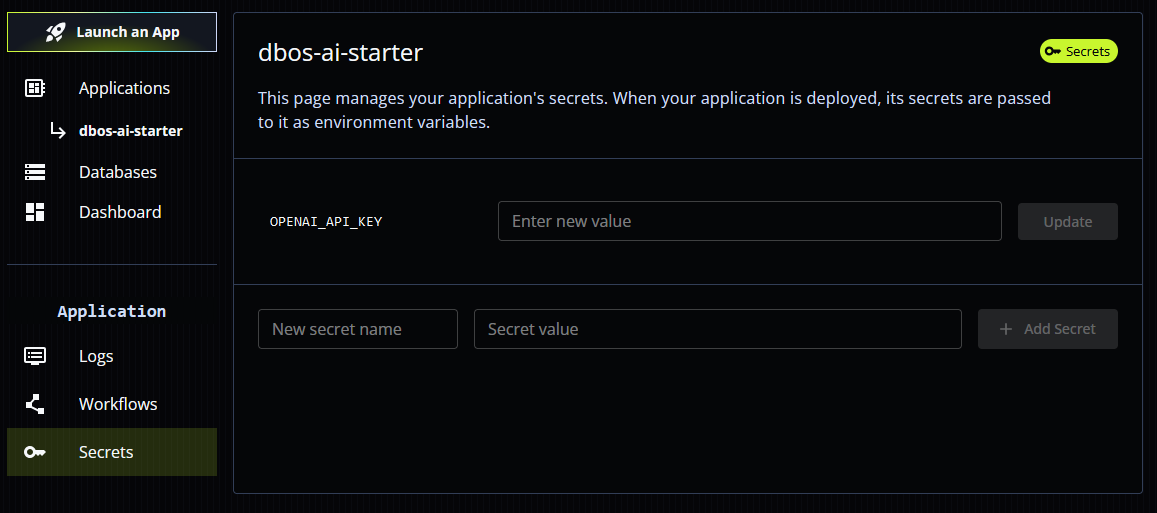
Additionally, you can manage your application's secrets from the secrets page of the cloud console.
Importing Secrets
You can import the contents of a .env file as secrets.
Allowed syntax for the .env file is described here. Note that interpolation is supported but command substitution and encryption are currently not.
Import a .env file with the following command:
dbos-cloud app env import -d <path-to-dotenv-file>
For example:
dbos-cloud app env import -d .env
Listing Secrets
You can list the names of your application's secrets with:
dbos-cloud app env list
Deleting a Secret
You can delete an environment variable with:
dbos-cloud app env delete -s <secret-name>